Can mobile mesh networks like goTenna’s be hacked?

In an era of increasing reliance on interconnected critical infrastructure systems, safeguarding power grids, gas pipelines, and transportation networks has never been more vital. These systems are often vulnerable to malware and other malicious hacking methods.
Most recently, Dutch researchers from cybersecurity firm Midnight Blue have identified vulnerabilities in the widely used TETRA radio technology, controlling critical infrastructure like power grids, gas pipelines, and transportation systems globally. Traditional communication methods, like centralized networks, are susceptible to single points of failure and cyberattacks, exposing critical infrastructure to potential disruptions.
How do mesh networks help solve this problem?
Mobile mesh networks offer an alternative by distributing communication capabilities across thousands of square miles of interconnected devices. The beauty of mobile mesh networks lies in their adaptability and self-healing capabilities. If a node becomes unavailable due to a disruption, the network can dynamically reroute information through alternative paths. This robustness is a game-changer, ensuring critical information reaches its destination, even in challenging conditions.
Moreover, the decentralized nature of mobile mesh networking devices makes them inherently secure. Traditional centralized networks are attractive targets for hackers aiming to stifle public infrastructure. In contrast, mobile mesh networks distribute data through easy-to-use, interoperable devices without relying on a single point of failure, making it considerably more difficult for malicious actors to pinpoint vulnerabilities.
What makes mobile mesh networks inherently secure?
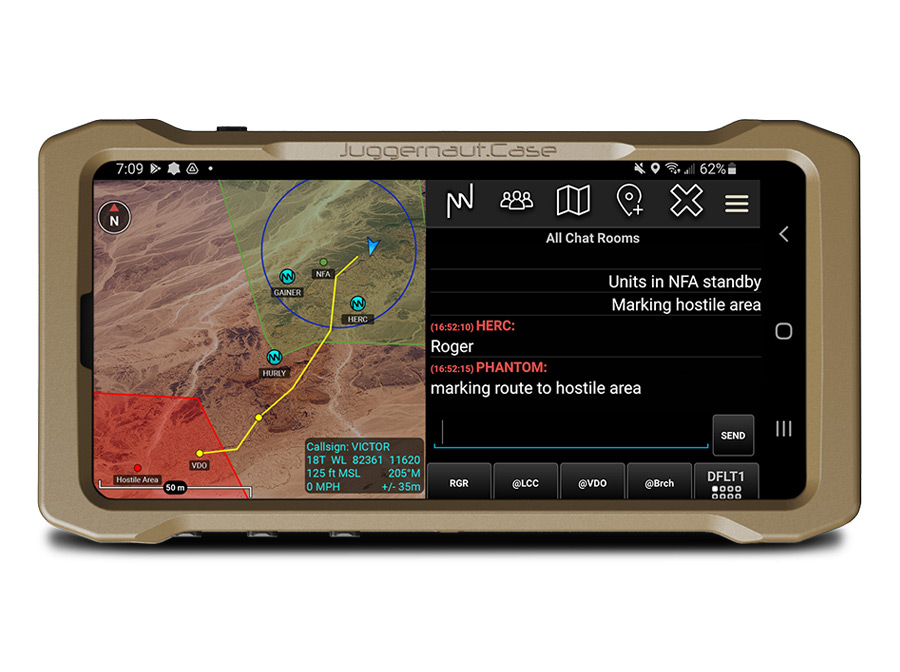
Take, for example, the goTenna Pro X2 mobile mesh networking device. It pairs with any Android or iPhone through an app and is used on the go without cell service, Wi-Fi, or satellite connectivity. If you intercept the signal, you must decrypt the data because the goTenna app natively utilizes 384-bit ECDH encryption (and eventually AES 256 encryption) for one-to-one messaging entirely off the grid. In addition to this layer of security, all of your transmissions wouldn’t be IP-based, further reducing the risk of interception.
How secure is the goTenna TAK plugin?
If the user wants to use the goTenna TAK plugin, users have the option to encrypt broadcast messages. The apps have a feature to create a unique AES 256 key. This key can be sent to other end-user devices either Over The Air (OTA) or by QR code. goTenna leverages FIPS-approved algorithms to support data in transport encryption and data at rest.
The goTenna TAK plugin uses a single encryption key that is configured within the app. The encryption keys are protected with the Android Keystore. Each goTenna Pro App and ATAK plugin instance generates a unique AES key to support data at rest encryption of local data and logs. AES 256 is specifically leveraged for private, group, and broadcast message encryption.
Where to harness the power of mobile mesh for critical infrastructure
When disasters strike and disparate groups converge to rescue survivors and deliver much-needed aid and relief, interoperability challenges are front and center. The most heavily used and relied-on form of communication often goes out right before the emergency response effort needs it the most.
In cases where traditional communications are flooded or unavailable, goTenna Pro Series mesh networking devices are cross-compatible. If five agencies bring their own goTenna devices, the radios can be rapidly and easily user-tuned to an encrypted, shared frequency through the TAK application or goTenna’s Pro App. This type of interoperability allows users to create a unified communications network that can transmit data to all relevant individual operators in any environment seamlessly and inexpensively.
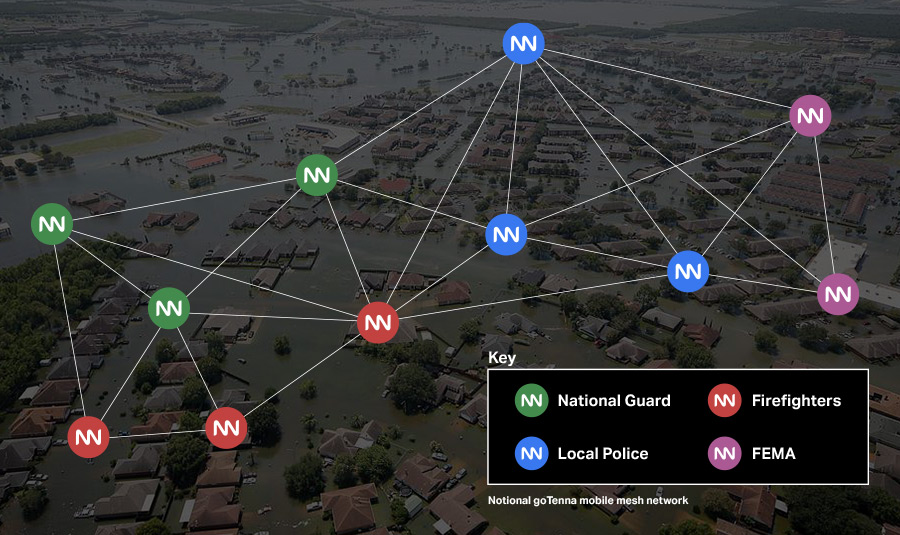
Gas pipelines, responsible for transporting energy resources across vast distances, are equally vulnerable. Mobile mesh networks can facilitate real-time monitoring and control, enabling immediate responses to leaks or anomalies. By leveraging sensors and nodes along the pipeline, operators can swiftly pinpoint issues and direct maintenance crews, minimizing environmental damage and ensuring public safety.
Transportation systems, including trains, buses, and airports, are the arteries of urban mobility. Interruptions can cause chaos and economic losses. Mobile mesh networks enable seamless communication between vehicles, infrastructure, and control centers. For instance, a malfunctioning signal on a train line can be swiftly communicated to other trains, preventing collisions and minimizing delays. To see how mobile mesh networks work underground, check out this previous article from The Last Mile here.
As we move towards a future where critical infrastructure is increasingly interconnected, the need for innovative solutions to safeguard these systems becomes paramount. Mobile mesh networks offer not only enhanced reliability and security but also scalability, adapting effortlessly to the growing demands of our modern world.
Governments, industries, and technology pioneers must collaborate to harness the power of mobile mesh networks and usher in an era of fortified critical infrastructure. By doing so, we can ensure that emergency personnel, gas pipelines, and transportation systems continue to operate reliably and securely, no matter the challenges that arise.







No Comment